How to secure your wi fi. How do you know who is connecting to the limit? Entry - WiFi connection
Today's drone-free measures play an important role in the lives of farmers. Just as 10 years ago it was essential to have an Internet cable for your laptop, today your phone connects to the Internet via Wi-Fi. Computers, laptops, netbooks, tablets, smartphones, printers - all of them can be connected to each other and communicate with each other simply in the air. And of course, such possession is not only with you, but with those who are absent. It is extremely important for him to take care to steal his dartless measure.
1. Protect the Wi-Fi network itself from the middle.
It is necessary to select a reliable type of security and install a collapsible security key. We recommend choosing WPA2-PSK and a security key with 8-10 characters.
Often we won’t even ask if you want wi-fi network. For whom check the box Enable hidden Wireless(Div fig. vishche)
In some cases, you can adjust the strength of the transmission so that the access point covers your apartment and does not reach your neighbors.

2. Protect the access point (or router)
on D-Link applications DIR-300:
Go to section MAINTENANCE, select a friend Device Administration, have adjusted Admin Password Please enter a new password:

And in the adjusted Administration uncheck Enable Remote Management To prevent the device from logging into the web interface from the Internet.
Today's third koristuvach of the world's pavutina It is widely planned to cover the entire booth, providing high-speed Internet access for all devices. And it’s true, why not use this ability when sitting in a chair, lying on the sofa, or in bed before going to bed, or accessing the Internet via a smartphone or.
In all practical situations, there is one big “ALE” - homeowners rarely adhere to security rules, which completely prevent access to Wi-Fi. Over the course of time, we begin to notice that the Internet connection speed has decreased, and the printer has started to print “nude photos”, sometimes misleading them! The operations of the “fryer”, which, having connected to your network, do not have easy access to the Internet or to the printer, may allow third-party clients to become accessible and more confidential information, for example, your money on electronic gamans. Therefore, ensuring the drone-free margin for yourself is the number one task, especially for the money-makers who are hanging around in a rich apartment.
How to ensure access to Wi-Fi from outside intrusion
Zazvichay koristuvach, having noted incorrect robot The computer is connected to the border, and the discount is in a hurry to stagnate. Perhaps, by analogy with system unit, like raptovo hung. And here we look for a thin object to reach the attached “Reset” button on the case hemstone ownership. Most often, such actions are reserved for a short term, and the situation hastens to repeat itself.
Ways to secure Wi-Fi access:
- With a head start, it will be easy to change the password for access to security. Even after configuration by the operator (or independent configuration), the device continues to save factory data. And here, you don’t need to be a “computer genius” to access the settings panel via the web interface!
Note! The ability to customize the panel with a router is not available on all models, so this is more practical for the Wiconian. - Now it is necessary to set a password for access until the limit. It is very important for you to select a cipher. Sometimes we insist on our weak memory, but with enviable consistency we throw it away!
It’s best to tweak the WPA2 encryption algorithm once and come up with a 10-digit password that you want to change. To do this, select a random set of letters and numbers, and simply write down the combination you come up with on a piece of paper or a box in your router.
Note! Do not create passwords that can be read. Nicknames and names in the English list are difficult to guess, but easy to pick! - You will no longer need to use the WPS function, which creates a digital PIN code for new devices. The function is active on most access point models. Is it possible for you to constantly connect different smartphones Or tablets, then folding ones are not to blame.
Note! However, if you need to regularly connect to new gadgets, it is enough to immediately enter the access password! Minimum fee for home security. - There is a recommendation to be more respectful. You need to correctly close the router’s web interface, so that you don’t just close the browser tab, but also “exit the browser panel.”
Such caution is associated with certain features of Internet browsers. When browsing pages, browsers save caches and cookies, which are responsible for saving time-sensitive files and information to the resource. You may have noted earlier that if you have abandoned the site, re-authorization is not required. So this is yet another loophole for an ill-tempered thief!
Note! It would be bad to take into account the clearing of the cache and browser cookies that you are actively exploiting (read the statistics for how to earn it:,). - The coming days are quickly addressed to the acknowledgments of the koristuvachs, the fragments of which may be part of the church. So, first of all, I’ll change the subnet of the router, the rest of it is installed for washing and seeing wealth. Call me, there is the address:
- 192.168.0.0
- 192.168.1.0
- 192.168.1.1
Moreover, the addresses are indicated on the device body; we don’t need to change the IP address via the web interface and the local date of the new name, instead of the factory one.

Vitannya! Having prepared an article that will summarize all the main points and most effectively satisfy your needs, How to steal Wi-Fi from a network. Who are we kidnapping? The type of neighbors is obvious, but if you need to steal the Wi-Fi network in the office, then from colleagues from the other company:). Well, if it’s serious, then the nutrition of the protection of dart-less measures is now even more relevant, which I have earned for the article in which I have described. The article quickly became popular and received a lot of comments.
We set a password to access the Wi-Fi router
Here's what you need to do when setting up your defense dartless Wi-Fi boundaries. When setting up the router, select the “System Tools” tab, then go to the “Password” tab.

Enter your old login and password, then enter your new login and new password in the form below. Create a good and flexible password. What does the letter and numbers add up to? Never mind, remember it yourself :). To save, press “Save”. You can continue to adjust the Wi-Fi network protection.
We set a password for the Wi-Fi network and set the encryption type
In the obligatory order, you need to specify the type of encryption that you use for the measure, and install reliable password. Well, what if you have a cafe and you want to earn money? Private access to Wi-Fi for business partners.
Go to the "Wireless" and "Wireless Security" tabs. For the WPA/WPA2 – Personal protocol, we put an icon, set the settings as in the screenshot below and in a row, like “PSK Password:” is visible good password. This password is used to connect to Wi-Fi. To save, press “Save”.

The router prompts you to re-enable it, but if you continue to make adjustments, you can not re-enable it yet. Any new adjustments will only work after re-installation.
Another miraculous way to heal. We need to name the Wi-Fi network, and you can only connect to it if you know what it’s called. Your measure does not appear in the list of available measures.
Let’s just go to the “Wireless” tab. And in order to add an SSID, simply uncheck the “Enable SSID Broadcast” item. The axis is so simple. Press the “Save” button to save changes.

Enables filtering of devices based on MAC address
Extending this function will allow you to connect only the same devices to the router MAC addresses and what is prescribed in the instructions and permitted. This is a very effective protection, but if you often connect new devices, it will not be very easy to immediately go into setting up the router and assign the MAC address to the device.
To get started, you need to find out the MAC addresses of the devices you want to allow connection to the Wi-Fi network. You can look at them in the settings, read the report. Whether it’s a phone or a tablet, you can look at the address in settings, in the “About phone” section. And if the device is already connected to the router, all necessary information can be found on the “DHCP” tab – “DHCP Clients List”.
Now, go to the “Wireless” tab and go to “Wireless MAC Filtering”. You can enable this service right away by pressing the “Enable” button. Then we set the icon to the item “Allow the stations specified by any enabled entries in the list to access.”. This means that only devices on the list can connect to Wi-Fi.
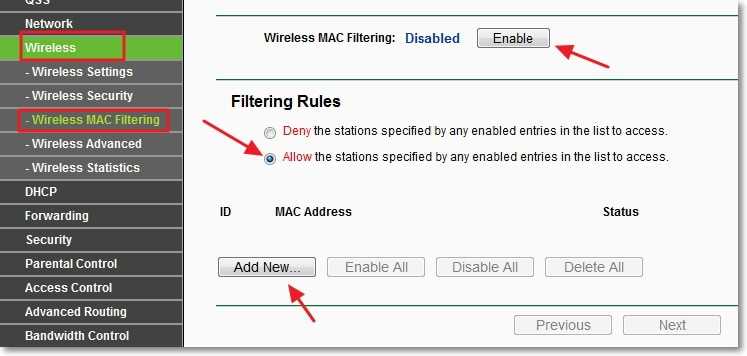
I press the “Add New...” button to add the MAC addresses of the devices that need to be allowed access. Enter the MAC address, description (behind the rules), disable the Enable status and press the “Save” button.

This method allows you to add all the devices you want to allow to connect to your router.
Enable QSS (WPS) service
I wrote in detail about this service, and about those who profit from it, in the statistics. If you don’t often connect new devices and it’s not difficult for you to enter the password for the Wi-Fi network, then it’s best to turn on this service.
To connect, go to the “QSS” tab; it may also be called “WPS”, or so it seems. I press the “Disabled QSS” button.

This is the last point that I would like to make for permanent protection of the Wi-Fi network on your router. You can only reactivate the router by clicking “click here” on the message, or use the button on the router itself.
Axis and all friends, all that I want to please you for your protection dartless lines. I hope that the information I have prepared for you will be of use to you. Good luck!
More on the site:
How to steal Wi-Fi? Main and effective reasons updated: Lyuty 7, 2018 by: admin
Today there will be a great conversation about how to create a safe border wi-fi booth, steal home computers, connections to this network, smartphones and tablets using the RT-N12VP application.
Now, let us know in advance that the protection of your dartless line is indicated by its weakest link. Today we're going wild until basic adjustments Don't worry about your troubles.
Let's say you have 2 at home desktop computer, 2 laptops, 3 tablets and 4 smartphones. Others, such as TV set-top boxes, wi-fi MFP I’m not talking about media center servers on Android.
Check that you have antivirus installed on all devices.
It's important. If one of the devices is infected, then the infection of others is on the right at the next hour. Thus, Android smartphones can carry advertising viruses local measures with great success.
You can turn on automatic search for mobile devices. On the right, you can become a victim of shahrays, who specially create open access points using the method of stealing data.
Clear the list of restrictions that are forgotten by your devices. Lose the familiar safe spaces: at home, at work.
To prevent theft of funds, “recovery” of mail account records, social measures On other sites, perhaps use two-factor authentication.
Well, you stole the devices, you didn’t waste the wi-fi on the voodoo of the shahrays from the “catless” ones. What's next? We have set up secure wi-fi.
The center of your all-world wi-fi near the apartment is your access point (router). In the vast majority of cases, the account is protected by password and login. Let's try to make your home Wi-Fi network more secure.
Installable Authentication method(River of safety) - WPA2-Personal
WPA-PSK key(password merezhi) - like this FD5#2dsa/dSx8z0*65FdqZzb38. So, it’s difficult to remember such a password, but it’s more important to remember it. On the right in what is the selection program wi-fi passwords I'll completely overdo it. Selecting a password in this time is on the right. On your smartphone, you can install a similar program, for example, and try, how many hours will pass before you select a password for your account.

Let's move on to adjustments Bezdrotov's measure — Filter MAC address of drone-free network
The MAC address filter of the drone-free network allows packets to be processed from devices with the same MAC address of the drone-free network.
To put it simply, your access point can only be connected to devices with MAC addresses that are allowed for connection. How do I get these addresses? You can look at the settings of the devices and enter them into the settings of the router. You can connect Wi-Fi through the skin, view the data that appears in the router’s network map and enter these addresses in the MAC address filter of the drone-free network.
Android smartphones have MAC addresses Setting up -> About the phone -> Secret information ->Wi-Fi MAC addresses.

If you live alone or, let’s face it, for a while, if you don’t bother with the dartless line, you can turn it on. These parameters are located in the section Bezdrotov's measure — Professionally

Same with the division Administration —System Access can be enabled via Telnetі web access from WAN. Therefore, it will be important to connect to the router. If the firewall is configured, then it will work.
There will be more.
Do you think that stealing your home WiFi with a strong password will save you from freeloaders. I hasten to disappoint you. This is not entirely true. No matter how cool your password is, the risk of connecting third parties is even greater.
How Russia loves freebies, I don’t need to explain to you). She herself comes up with so many brilliant ideas. While for some this idea is good, for others it can be a real headache.
How can the danger of a drone-free unit turn out?
Everything here is left to the imagination of a freeloader. In one case, it costs expensive traffic, in another, access to your data, both the computer itself and Internet resources (mail, social networks, etc.)
How to secure your home WiFi without third party connections?
In fact, it is possible to get rid of money without delay, but if you maintain basic safety standards, you will be able to eliminate such a bastard and definitely not become a victim of an amateur. Let's take a look two simplest way. The first and most obvious one I recommend is this set up correctly router, the other - vikoristannya special programs.
Setting up the router
The main difference is wifi – this is the protocol wps. If there is no interference, there is practically nothing to turbocharge. On the other hand, since you can’t turn it on, everything else is for your peace of mind.
A) For encryption, use the WPA2 algorithm. Of course, you can grind it wpa2, Ale resources and wasted this hour without using the method. He is not an agent of the special services, who needs it. If your device does not support qiu technology, then think, ladies, even under the threat of home security.
b) Vikorist the correct password. I wrote a whole book about the importance of a strong password, but if you can, I recommend reading the article. As a rule, access to setting up the router can be denied by typing it into the address bar of the browser. 192.168.1.1 , where is your account name/password → admin and 1234 vid. Such passwords can be cracked in seconds. Vikorist any combination of 8 characters (numbers, letters, signs).
c) Welcome to the border(Get the SSID). This point is obligatory, since it is considered ineffective, otherwise it will be obvious. In the settings of the router, select “Get SSID”. This is your limit, as we are most likely, scanning the space in search of a WiFi measure. Knowing this, you can connect to this or that other WiFi boundaries. In the authorities of the drone-free network (the “connections” tab), select the current settings.
Well, and finally - for the paranoid rogues of total security: you can adjust the barrier so that only people have access singing annexes, And then, two front rows passed, all of them were not allowed in the middle. For which you need to filter for MAC addresses of devices.
The names of the sections and options on different routers and the access point are different, otherwise the place is lost by yourself.
Another way is to use special programs, such as a butt utility. The program was created to help owners of home WiFi hotspots who want to control the connections of third-party devices. The program runs on Windows, Mac OS X and Linux.
The program displays a list of active devices. Green color→ allowed/known devices, red → unknown.
Great recommendations. Get your act together, don't be rude private access» to folders, files and printers, and if you open it, close it immediately as you will not need it. Before speaking, the procedure can be verified as follows: panel of the bathroom → center of the bathroom with edges and underground access.

